The Hows of Enhancing Cyber Threat Detection and Response Capability

After spending millions of dollars on purchasing and managing various security technologies and other components, organizations are struggling to have good visibility into their threat landscape with blind spots all over the place. Such blind spots lead to cyber attacks slipping through the sensor grid along with considerable delays in containing and eradicating them once they occur.
During my 22 years of experience in cybersecurity, specifically cyber defense, I have worked with various clients from across the world. All of them struggle with a lot of questions when it comes to threat detection and response capabilities. Which log sources should we collect and monitor? Is monitoring everything the best practice to have greater visibility? How should threat intelligence be used? And many more. I reflected on these questions and tried to find answers to them by asking another question to myself. What are the key elements of a good threat detection and response capability, that could enable organizations to have greater visibility and the ability to swiftly respond to cyber threats?
I took the approach of looking at the various characteristics (Tactics, Techniques, and Procedures aka TTP) of modern cyber attacks. Through my experience, knowledge, and research, I came up with 8 essential elements of good threat detection and response:
- Endpoint Telemetry
- Network Telemetry
- User and Entity Behaviour Telemetry
- Targeted Attack Detection
- Threat Intelligence
- Contextual Information
- Cyber Analytics
- Orchestration and Automation
By looking at various cybersecurity breaches and compromises you will notice that all of these attacks have one or more of the above elements. Such attacks include an account compromise, exploitation of a vulnerability on an endpoint, credential dumping, lateral movement over the network, file encryption, and data exfiltration over the network.
I have worked out a Threat Detection and Response (TDR) stack that covers the 8 essential threat detection and response elements that could drive great visibility into cyber threats as well as the ability to swiftly respond to cyber attacks.
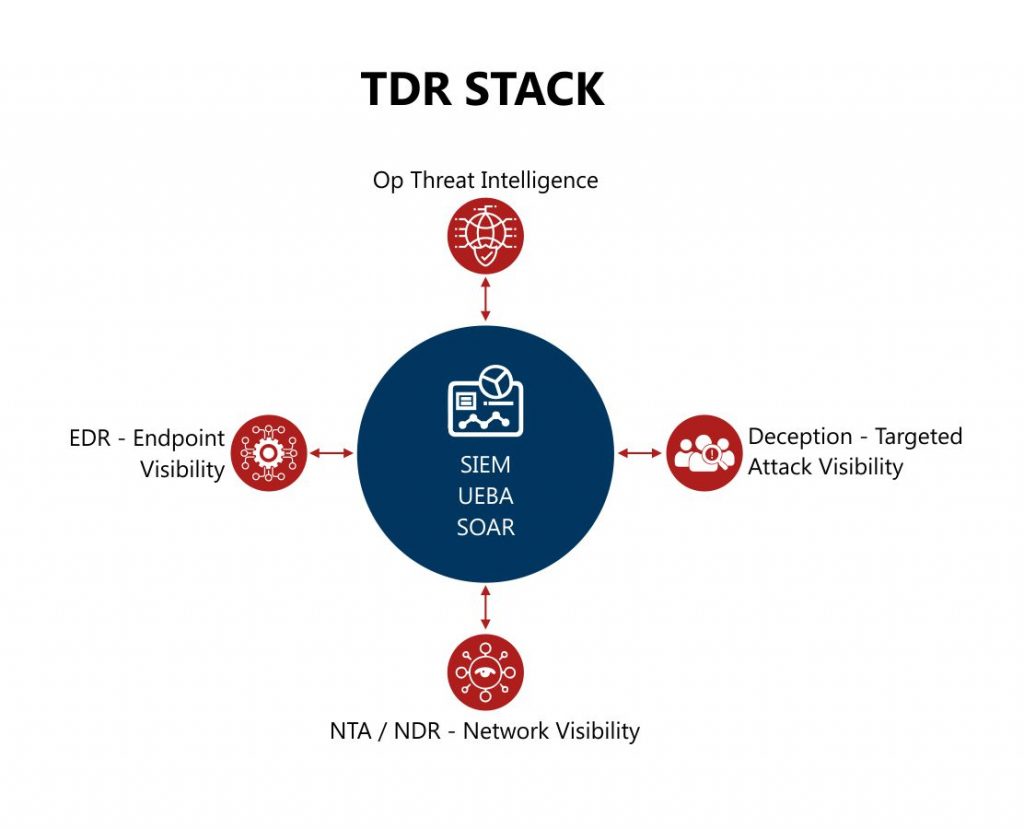
Endpoint Detection and Response (EDR)
To capture and make sense of endpoint telemetry, I have included an Endpoint Detection and Response (EDR) component in the stack. An EDR solution is a great tool to capture all events happening on an endpoint and provide complete visibility into endpoint attacks. Modern EDRs have machine learning capabilities to detect behaviour-based attacks as well. They are also good at blocking attacks based on signatures, indicators of compromise (IoCs), and behaviour. Some EDR tools also provide host forensic capabilities which are great to have during a security incident investigation.
Network Traffic Analyzer (NTA) / Network Detection and Response (NDR)
While EDR provides good visibility into the endpoints, there are some challenges too. It needs an agent to be installed on the endpoint to capture the events. In a modern workplace, there are systems on the network – such as IoT devices for example, that do not support agent installation. Another challenge that is seen with EDR tools is that an attacker can disable an EDR agent, hence creating a blind spot in threat detection. To address these challenges and have good network visibility, I have included network traffic analyzer (NTA) / Network Detection and Response (NDR) in the stack.
NTA / NDR tools are great at providing network telemetry visibility. NDR tools can also assist in responding to network attacks.
Deception
Attack vectors are becoming complex and sophisticated day by day. It is very important to detect the attacks as early as possible. Deception technology is a great way to complement EDR and NDR solutions in detecting attacks early and providing greater context around attack techniques used by the adversaries.
Deception technology also reduces alert fatigue by generating 100% true positive alerts. A hit on this technology means that the organization has a confirmed compromise. Deception technology enables an organization to deploy honeypots, honey users, honey credentials, and honey files to detect attacker activities earlier in the attack chain. It can also provide targeted attack visibility. This is the third component of the stack.
Operational Threat Intelligence
Operational threat intelligence is the next component of the TDR stack. Cyber threat intelligence means different things to different people. In my experience, the best use of threat intelligence is when it is operationalized. An operationalized threat intelligence has three main characteristics.
First, threat intelligence should be utilized to build an organization’s threat profile by identifying the threat actors, vectors, and TTPs specific to the organization. Second, it should regularly identify IoCs to be included in the sensor grid to detect and, where applicable, block them throughout the organization. Third, threat intelligence should contribute towards enhancing the cyber threat detection capability of the organization. This could be accomplished through building new detection use-cases in SIEM, EDR and NDR, for example. Operational threat intelligence also enhances an organization’s threat hunting capability.
SIEM, UEBA and SOAR
The next component is the central nervous system of the TDR stack which brings everything together, similar to what the brain does for the human body. It has three functions: SIEM / Cyber Analytics, User and Entity Behaviour Analytics, along with Orchestration and Automation. These components provide a single pane of glass view for the endpoints, network, targeted attacks, users, and entity telemetry. The cyber analytics function utilizes machine learning / behavioural algorithms and event chaining capabilities to identify the most anomalous events in an organization and help the security operations teams to focus on them instead of reviewing and investigating hundreds/thousands of individual alerts/events to manually link the alerts to an incident. The next-generation SIEM solutions have these capabilities (cyber analytics) provided they are configured properly to perform these functions. Orchestration and automation constitute another critical function of the central nervous system that helps in enriching the information context, automating the analysis, and responding to threats by assisting in containment, eradication, and recovery.
By now, you can see how the Threat Detection and Response (TDR) stack provides comprehensive threat visibility, and the ability to swiftly investigate and respond to cyber attacks.
I hope this article has provided you insight into enhancing your threat detection and response capability.